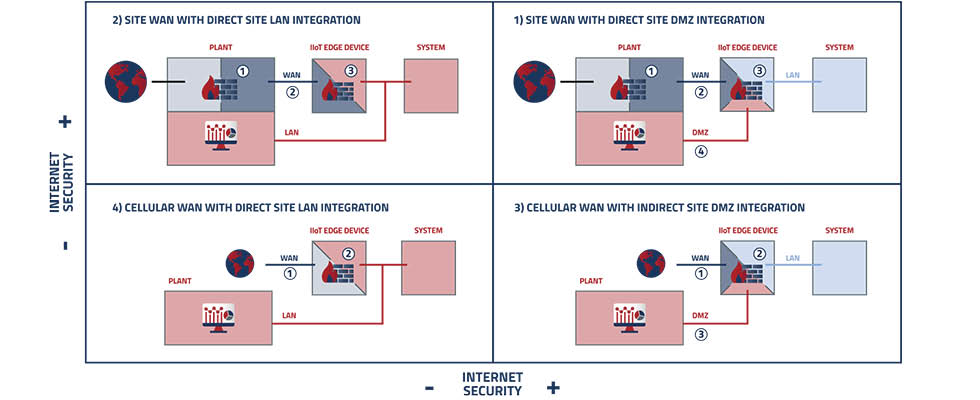
Industrial internet of things (IIoT) connections must handle multiple nodes of connectivity securely. To achieve this, users can implement one of four distinct network topologies.
From most to least secure, the topologies are ranked as follows:
- plant internet connectivity to an IIoT edge device with demilitarized zone (DMZ) segregated connection to plant supervisory control and data acquisition (SCADA)
- plant internet connectivity to an IIoT edge device with direct local area network (LAN) connection to plant SCADA
- cellular internet connectivity to an IIoT edge device with DMZ segregated connection to plant SCADA
- cellular internet connectivity to an IIoT edge device with direct LAN connection to plant SCADA
In these arrangements, there are two major differences: source of internet connectivity to the IIoT edge device
and mode of system connectivity to plant SCADA.
Source of Internet Connectivity to the IIoT Edge Device
Internet connectivity to the IIoT edge device can be sourced from either the plant’s wide area network (WAN) or a cellular signal from a regional internet service provider (ISP).
For security reasons, the WAN option is advised. It allows users to implement extra security measures before connecting the IIoT edge device to the internet.
Plant WAN
When using plant WAN for internet connectivity to IIoT edge devices, the connection should be completely firewalled, except for the following minimum network requirements:
- public internet access via a Class A, B or C private network
- virtual private network (VPN) traffic allowed via transmission control protocol/internet protocol (TCP/IP)
- Port 1194
- message queuing telemetry transport (MQTT)-over-transport layer security/secure sockets layer (TLS/SSL) traffic allowed via TCP/IP Port 8883
- domain name system (DNS) resolution and free traffic towards VPN and data acquisition servers
- encrypted traffic allowed
If the plant’s internet connectivity for the IIoT edge device does not meet these minimum network requirements, some or all features of the IIoT application may be compromised or unavailable.
Cellular signal
When internet connectivity for IIoT edge devices is sourced through a cellular signal from a regional ISP, the plant owner or operator should manage the service contract. This allows for better administrative control over internet connectivity within the plant’s domain. Consider implementing the following security measures:
- disabling or blocking voice services
- disabling or blocking peer-to-peer (P2P) short message service (SMS) services
- imposing data caps to regulate and monitor how much data is transferred
- choosing cellular internet service providers (ISPs) that incorporate real-time monitoring and anomaly detection
Typically, IoT-focused cellular connectivity providers offer network firewalls that restrict data services accessible by devices. For example, they allow traffic only to specific IP addresses or ranges. This effectively limits the SIM card’s data service to its intended application.
Mode of System Connectivity to Plant SCADA
System connectivity to a plant’s SCADA may be implemented via either a DMZ segregated connection to plant SCADA or a direct LAN connection to plant SCADA.
The DMZ option is advised. It allows users to implement extra security measures and provides more flexibility between the system and the plant’s SCADA network.
DMZ segregated connection to plant SCADA
When using a segregated DMZ connection, the following additional security measures and flexibility can be applied: stateful firewalled routing, network address translation (NAT) or completely disabled routing between WAN and DMZ.
Direct LAN connection to plant SCADA
When using LAN, the plant owner or operator should implement stateful routing rules for traffic between the system and the SCADA application. This provides better administrative control over data traffic monitoring within the plant’s domain.
Consider incorporating the following security measures:
- packet filtering: IP address, packet type, port number, etc.
- circuit-level filtering: TCP handshake and protocol monitoring, etc.
- stateful firewall routing: entire session monitoring of IP addresses and payloads, etc.
Functional Applications for Data Transmission
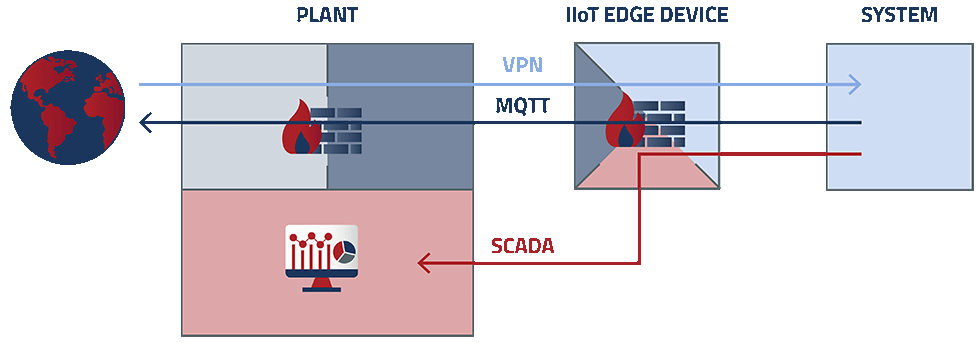
In topology 1 above, data transmission between the IIoT edge device, the internet, the plant and the system involves three distinct functional applications—VPN data transmission between the internet and the system, MQTT data transmission between the system and the internet and SCADA integration protocol between the system and the plant.
VPN data transmission between the internet and the system
IIoT edge devices offer powerful ways to enable VPN connectivity by using the onboard input/output (I/O). In cases where the end user needs complete control over making remote access available, a physical switch can be used to enable and disable VPN access to the industrial application.
MQTT data transmission between the system and the internet
This connection enables data transmission for the IIoT application. Selected system data tags related to performance metrics and process variables (such as flow, pressure, temperature, component status, alarm history, etc.) are extracted and sent to the MQTT broker of choice for data analytics, reporting and dashboard visualization. IIoT edge devices can be configured to create multiple tag groups and enable different data transmission intervals and conditions based on user requirements.
SCADA integration protocol between the system and the plant
This connection facilitates data transmission between the system and the plant’s SCADA using IP-based communication protocols, such as OPC-UA, ModbusTCP and ProfiNet, among others.


